phpMyAdmin multiple XSS - Transformations
- Reported: 08.07.2011
- Published: not yet
- Updated: not yet
- Affected versions: 3.4.x
- Risk: medium to high in multi-user environments
- Solution: no solution
- CVE-ID: none
Description
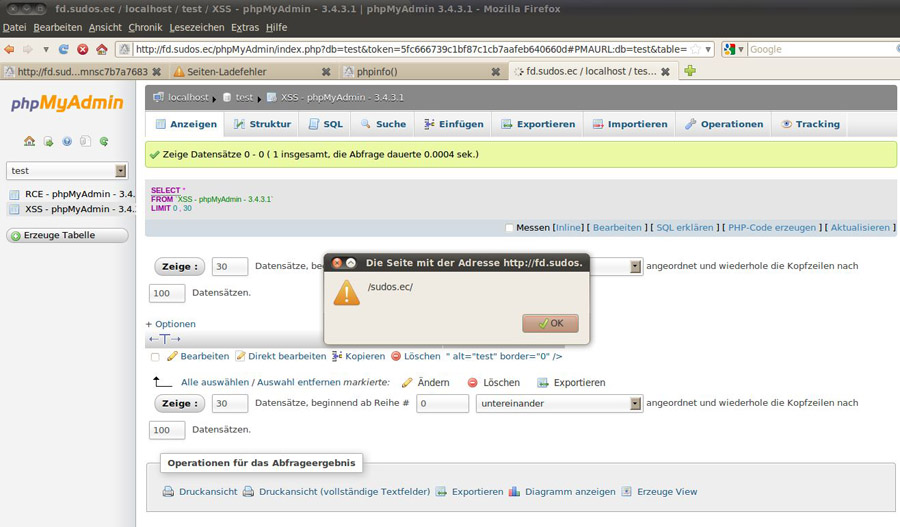
The new transformation feature in phpMyAdmin is prone to multiple XSS due to insufficient escaping.
The affected parameter is the "transformation_option" parameter. There are several files, which takes these options and display them to the user, without any escaping.
The value inserted into the table, is also displayed unescaped, if you use the transformation feature.
This allows an attacker to execute arbitary javascript code within site context.
The attacker needs access to the victims database and the CREATE or ALTER TABLE right. Furthermore, the transformation feature has to be enabled.
Additionally, the attacker must trick the victim into opening the following link (list the contents of the table)
- File: phpMyAdmin3/libraries/transformations/image_png__inline.inc.php
- Line: 16-27
function PMA_transformation_image_jpeg__inline($buffer, $options = array(), $meta = '') {
require_once './libraries/transformations/global.inc.php';
if (PMA_IS_GD2) {
$transform_options = array ('string' => '<a href="transformation_wrapper.php' . $options['wrapper_link'] . '" target="_blank"><img src="transformation_wrapper.php' . $options['wrapper_link'] . '&resize=jpeg&newWidth=' . (isset($options[0]) ? $options[0] : '100') . '&newHeight=' . (isset($options[1]) ? $options[1] : 100) . '" alt="[__BUFFER__]" border="0" /></a>');
} else {
$transform_options = array ('string' => '<img src="transformation_wrapper.php' . $options['wrapper_link'] . '" alt="[__BUFFER__]" width="320" height="240" />');
}
$buffer = PMA_transformation_global_html_replace($buffer, $transform_options);
return $buffer;
}
You should be aware of, that $buffer and $options are userinput and have to be escaped, whenever and wherever you use it.
It not only effects image_png__inline.inc.php, but also other transformation features like: image_jpeg__inline.inc.php, text_plain__imagelink.inc.php, text_plain__link.inc.php, ... and so on.